1. What does unauthorised access mean?
Unauthorised access is where no-one has permission to access any
files which are confidential or personal without consent.
2. Give two examples of unauthorised
access.
Two examples of unauthorised access are hackers going into your
files in order to seek information which may be some use to them without
authorised access. These can include: medical records, exam results, financial
information, other employee’s wages, and so on.
3. What is meant by sensitive files?
Sensitive files are files which are confidential and contain
personal information which you do not wish to share and have strictly
unauthorised to them. These can be medical records for example, as people do
not wish to publish personal information.
4. Give two examples of this.
Two examples of sensitive files include:
Address, phone number, work number, salary, medical records, your
will, job title, etc.
5. The
business: how can an
organisation such as a school use the network login to make sure that only
authorised users have access to sensitive files?
In order to make sure only authorised users have access to
sensitive files, they use self registration. This is where if workers wish to
have permission to an unauthorised file then they’d have to ask permission in
order to do so. If they enter the file without consent then they’ll be given
the title ‘hacker’.
6. In
business: which two
groups of people might want to gain unauthorised access to sensitive files?
Workers who are lower down in the work industry who wishes to
have more access to sensitive files compared to the manger and senior managers
above them and other fellow employee’s that are in rival with the other workers
will want to gain access so they can find information about the other’s salary
and wages. There are hackers within the industry and those outside the
organisation, and there is anonymous hackers who hack into the company’s
account in order to prove that the company’s security is poor. Or even
anonymous hackers from rival companies to find out the other company’s secrets
on their successful business.
7. What does a fire wall do?
A firewall decides what people can access your files and which
files they can’t. If there is a file which is unrecognised and if you don’t
know who an administer is, then the firewall blocks them from entering your
sensitive files so no confidential information is exposed.
The levels of security depends on the setting you set it on, and
stops applications from accessing your network without authorised permission
and blocks threats from attacking the computer. The firewall stops unknown IP
addresses and networks from accessing the company’s files. It stops traffic
from the input to the output.
8. What specific problems do banks
have? Describe a product which the
banks can use to keep their files safe?
A bank can use firewall software in order to stop the lower down
workers in the industry from accessing any information they don’t want them to
see. This can be information such as, how much money the bank has in store,
potential customers and their bank balance, salaries. Also hackers would want
to access this information and perhaps even customers of the bank. Another
major problem for banks is that people can use identity theft in order to get
information about another client to access their banking balance and
information. Using a firewall stops workers from accessing sensitive files and
stops hackers from entering the network. When people do online banking them use
an identity key to protect information and have security cameras at ATM’s to
stop theft.
9. You: how can you make sure that
unauthorised people don’t see your files?
The first way you can
protect your files from unauthorised access is to put a password on all your
files so only you know the password and the internal or external hacker cannot
connect to your network. Frequently update your software on your computer so
you are less at risk of your files being exposed to attack from hackers.
Hardware and software firewalls are also an option too. Hardware firewalls are
usually a device connected to your network on your router so no-one can enter
your network. Software firewalls are installed onto the computer and controls
the amount of ingoing and outgoing data so no anonymous servers are allowed
authorised access to your files. Nowadays it is becoming more common to
download a security virus protector on any device they own, as it stops
viruses, spy wares, Trojans and malware’s from damaging your files and computer
data. For example, these can be:
·
AVG
·
Norton
·
McAfee
·
Kaspersky
·
Bullguard and so on.
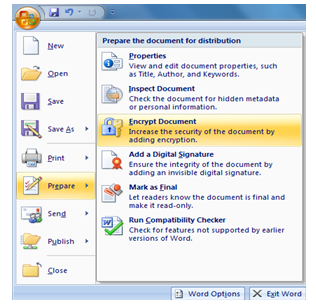
Put a password on a document
On your Microsoft
Word or Excel document, click on the ‘File’
tab on the top-left hand side of the document. Then go down to the ‘Info’
option and on the right there is an option which says ‘Permissions’.
On this tab, click on ‘Encrypt with
Password’.
You then decide on a password and confirm it and then
officially have a password for that Excel or Word document. However, if you
forget your password you cannot retrieve it or view your document again.
To: All teaching staff
CC: Office manager
From: Annie Clark
Date: 12th October 2013
Subject: Protecting files from unauthorised loss
Dear all
teaching staff,
It has come
to my attention that the files which the workers keep on their server are at
high risk of internal and external hackers which are eager to find confidential
information about the school’s finance records and salary information. We have
to take action towards this and have come up with two strategies of how to do
this. The first idea is to encrypt a password to all of your files and
documents whether this be a PowerPoint, Excel, Publisher, or Word document; as
demonstrated above. Another suggestion is t0 install a firewall on every server
on the Knight Templar’s network so it picks up the incoming and outgoing
traffic from the internet to the device and stops unknown servers from
accessing sensitive files that are unauthorised.
Kind
regards,
Annie Clark.










No comments:
Post a Comment